analyze malware
- Huge database of samples and IOCs
- Custom VM setup
- Unlimited submissions
- Interactive approach
| File name: | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe |
| Full analysis: | https://app.any.run/tasks/b29e585b-ea5b-4925-b3fb-cc980a1c2fbb |
| Verdict: | Malicious activity |
| Analysis date: | May 04, 2024, 02:25:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8B873B01BBA12B49F93BD403DD8EB75C |
| SHA1: | 244A445C05D910F97C6F7812BADBFF03E8746208 |
| SHA256: | 32AC9F3DBDA0ED38D564408BFA9C5537DA054A03F7D36BC9696D45FD84FA3F59 |
| SSDEEP: | 393216:6+SuMo7PoadOynG5XUVKDosb9A4PF2OY2EFQ+AehyES3Xs6:6+W1EQXUVKMsfPF2VXFZk13Xs6 |
MALICIOUS
Drops the executable file immediately after the start
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6588)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6732)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Steals credentials from Web Browsers
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Registers / Runs the DLL via REGSVR32.EXE
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Actions looks like stealing of personal data
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
SUSPICIOUS
Reads security settings of Internet Explorer
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6616)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Reads the date of Windows installation
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6616)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Executable content was dropped or overwritten
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6732)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Reads the Windows owner or organization settings
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Process drops SQLite DLL files
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Reads the BIOS version
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Checks Windows Trust Settings
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Access to an unwanted program domain was detected
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Reads browser cookies
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 5576)
- regsvr32.exe (PID: 5524)
- regsvr32.exe (PID: 6356)
- regsvr32.exe (PID: 2116)
- regsvr32.exe (PID: 1604)
- regsvr32.exe (PID: 5784)
Adds/modifies Windows certificates
- Integrator.exe (PID: 6472)
Starts CMD.EXE for commands execution
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
INFO
Checks supported languages
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6616)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6588)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6732)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
- identity_helper.exe (PID: 7692)
Reads the computer name
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6616)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
- identity_helper.exe (PID: 7692)
Create files in a temporary directory
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6588)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe (PID: 6732)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Process checks computer location settings
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6616)
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Reads Environment values
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Reads Windows Product ID
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Reads the machine GUID from the registry
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
Reads Microsoft Office registry keys
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- msedge.exe (PID: 3956)
Creates files in the program directory
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Checks proxy server information
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
Creates files or folders in the user directory
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
Reads the software policy settings
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
- Integrator.exe (PID: 6472)
- DiskDefrag.exe (PID: 5852)
- slui.exe (PID: 3044)
Creates a software uninstall entry
- 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp (PID: 6764)
Drops the executable file immediately after the start
- msedge.exe (PID: 3956)
Application launched itself
- msedge.exe (PID: 3956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (42.6) |
|---|---|---|
| .exe | | | Win16/32 Executable Delphi generic (19.5) |
| .exe | | | Generic Win/DOS Executable (18.9) |
| .exe | | | DOS Executable Generic (18.9) |
EXIF
EXE
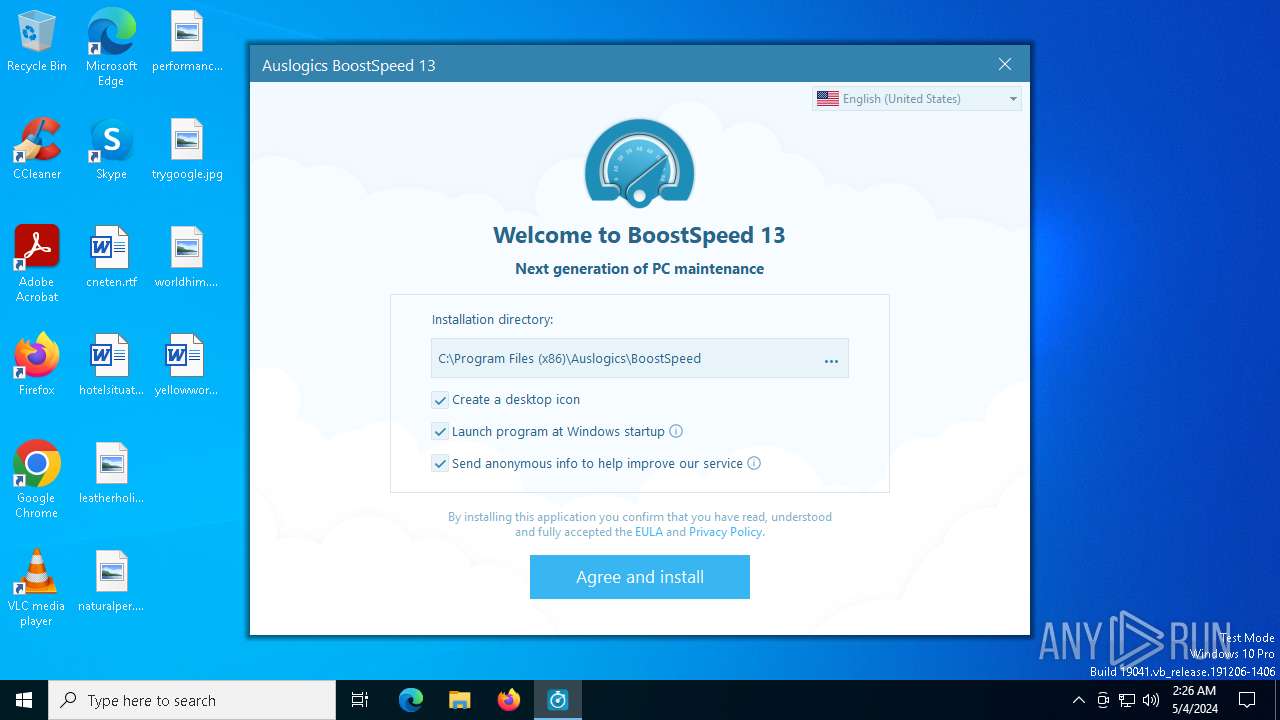
| InternalName: | boost-speed-setup |
|---|---|
| OriginalFileName: | boost-speed-setup.exe |
| ProductVersion: | 13.0.0.7 |
| ProductName: | Auslogics BoostSpeed |
| LegalCopyright: | Copyright © 2008-2024 Auslogics Labs Pty Ltd |
| FileVersion: | 13.x |
| FileDescription: | Auslogics BoostSpeed Installation File |
| CompanyName: | Auslogics |
| Comments: | This installation was built with Inno Setup. |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 13.0.0.7 |
| FileVersionNumber: | 13.0.0.7 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 5 |
| ImageVersion: | 6 |
| OSVersion: | 5 |
| EntryPoint: | 0x117dc |
| UninitializedDataSize: | - |
| InitializedDataSize: | 438272 |
| CodeSize: | 66560 |
| LinkerVersion: | 2.25 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| TimeStamp: | 2016:04:06 14:39:04+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Total processes
179
Monitored processes
53
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 6588 | "C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe" | C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | — | explorer.exe | |||||||||||
User: admin Company: Auslogics Integrity Level: MEDIUM Description: Auslogics BoostSpeed Installation File Version: 13.x Modules
| |||||||||||||||
| 6616 | "C:\Users\admin\AppData\Local\Temp\is-7R164.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp" /SL5="$70286,39312966,505856,C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe" | C:\Users\admin\AppData\Local\Temp\is-7R164.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | — | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6732 | "C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe" /SPAWNWND=$501D2 /NOTIFYWND=$70286 | C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | ||||||||||||
User: admin Company: Auslogics Integrity Level: HIGH Description: Auslogics BoostSpeed Installation File Version: 13.x Modules
| |||||||||||||||
| 6764 | "C:\Users\admin\AppData\Local\Temp\is-8DJOJ.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp" /SL5="$4029A,39312966,505856,C:\Users\admin\AppData\Local\Temp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe" /SPAWNWND=$501D2 /NOTIFYWND=$70286 | C:\Users\admin\AppData\Local\Temp\is-8DJOJ.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 5064 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3044 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5576 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Auslogics\BoostSpeed\DiskDoctorChecker.x64.dll" | C:\Windows\System32\regsvr32.exe | — | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1604 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Auslogics\BoostSpeed\DiskDoctorChecker.x32.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6356 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Auslogics\BoostSpeed\TaskManagerHelper.Agent.x64.dll" | C:\Windows\System32\regsvr32.exe | — | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2116 | "C:\WINDOWS\system32\regsvr32.exe" /s "C:\Program Files (x86)\Auslogics\BoostSpeed\TaskManagerHelper.Agent.x32.dll" | C:\Windows\SysWOW64\regsvr32.exe | — | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
30 245
Read events
30 051
Write events
177
Delete events
17
Modification events
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Auslogics\BoostSpeed\13.x\Settings |
| Operation: | write | Name: | General.Tracking.Param_UTMSource |
Value: boost-speed-13 | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Auslogics\BoostSpeed\13.x\Settings |
| Operation: | write | Name: | General.Tracking.URLMarkers |
Value: boostspeednosid | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{6D484312-01A3-96B5-2103-BEE119819358}\Version |
| Operation: | write | Name: | Assembly |
Value: 564A9B4BCDC4D84E951C74CF13863307564A9B4BCDC4D84E951C74CF1386330788AD8CBB5ED3F66B83A8A2CDF194269C890BB34AEBD806E41A50D3BD9C0B4765219909F09E75DEC0927FF4E8152284CD219909F09E75DEC0927FF4E8152284CD59B5414605BAE21E9735786EB516D3F8DE1283C2AFF9BF99D33ED2740C86BBD2F8157495FE950FA4A01046BB55F00DAD0F20AA1B1ADFE602954529934D03147D | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Auslogics\BoostSpeed\13.x\Settings |
| Operation: | write | Name: | General.Language |
Value: ENU | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Auslogics |
| Operation: | write | Name: | ClientID |
Value: {E43C4ED3-E46D-4DFF-BE4E-4ABDAD1553D8} | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6764) 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
173
Suspicious files
67
Text files
64
Unknown types
77
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6588 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | C:\Users\admin\AppData\Local\Temp\is-7R164.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | — | |
MD5:— | SHA256:— | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\SetupCustom.dll | executable | |
MD5:EB7147914DC4C26AB23A98C8BA1E1421 | SHA256:7FF5CD98CB5B533F730C44598CAF0E56864CA74ED680F75B47481BAEFB750BC6 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\AxComponentsRTL.bpl | executable | |
MD5:6C7439C8A20335AB9AC0FDA6AC35F0A1 | SHA256:88FCE4B08949148778BD8D786E9FE8455E7DABD2A08B0F72789EE1921E25114D | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\Integrator.exe | executable | |
MD5:7DDB9A2AE53CB9DD01C3500E156E2105 | SHA256:D8BEB0E3CD69F87AF5445E6547C9C0254D37DAD873C4E41ECCF576F71F478005 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\Localizer.dll | executable | |
MD5:E6873873E6C6A6F85B4B1685520E9206 | SHA256:828C205449939C0E6A04C462A11B4722A2D1471F610C43CBE5994188CC8CCEFB | |||
| 6732 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.exe | C:\Users\admin\AppData\Local\Temp\is-8DJOJ.tmp\32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | executable | |
MD5:8DAB0E0D4C0CE791982387A356FF20A7 | SHA256:D822A0A4162604999AF13B865ABD9612C6D2E1BC72D5B836DCF17DC59FA14B33 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\AxComponentsVCL.bpl | binary | |
MD5:7A824C04389D7F751FB189794E071BF9 | SHA256:498919B3B69C3E1FE50B627422BB130763428F0A54C69C00C887BCAE80157E34 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\BrowserHelper.dll | executable | |
MD5:6980E4ABC9727A284280EB58791D6CDE | SHA256:4822BA23988E058AB370457ACB97667A31A1FE69E36EA1D91D06572436DDBD38 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\sqlite3.dll | executable | |
MD5:C23F7E46FE37172BFB8D285C5BD3CF81 | SHA256:4A8D3F514123F0E3E0030E96830BE3E66450CBD91877D0099B23308978F44EE7 | |||
| 6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | C:\Users\admin\AppData\Local\Temp\is-AEFE6.tmp\CFAHelper.dll | executable | |
MD5:007E06C81AB17EB28DCB469C9ED81D1E | SHA256:37BCE388E1A9A1705A73B8FF9915DCF1606E18C5504D611A33571EF817D06A44 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
34
TCP/UDP connections
116
DNS requests
94
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | POST | 200 | 142.250.184.238:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
5800 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | unknown |
6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | GET | 200 | 192.229.221.95:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRJiUKgT2m88fZ4nxc1Lu6M%2FjvkagQUDNtsgkkPSmcKuBTuesRIUojrVjgCEAdpVDZkciT8g1iEeh8ZYO0%3D | unknown | — | — | unknown |
6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | POST | 200 | 142.250.184.238:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
5800 | SIHClient.exe | GET | 200 | 88.221.125.143:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | unknown |
5952 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
6472 | Integrator.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | unknown |
6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | POST | 200 | 142.250.184.238:80 | http://www.google-analytics.com/collect | unknown | — | — | unknown |
4680 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | — | — | unknown |
6764 | 32ac9f3dbda0ed38d564408bfa9c5537da054a03f7d36bc9696d45fd84fa3f59.tmp | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAsllCLO2YEqFaBOmVKKDvo%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | unknown |
4364 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2392 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5140 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
5952 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
4680 | SearchApp.exe | 104.126.37.145:443 | www.bing.com | Akamai International B.V. | DE | unknown |
5196 | svchost.exe | 20.190.159.75:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5196 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
r.bing.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
www.auslogics.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
status.rapidssl.com |
| shared |
Threats
1 ETPRO signatures available at the full report